Android users may need supplementary apps to perform the hands-on file manipulation one might expect from a robust operating system.
Answer the following statement true (T) or false (F)
True
You might also like to view...
The relation shown in Figure 15.12 describes hospitals (hospitalName) that require certain items (itemDescription), which are supplied by suppliers (supplierNo) to the hospitals (hospitalName). Furthermore, whenever a hospital (h) requires a certain item (i) and a supplier (s) supplies that item (i) and the supplier (s) already supplies at least one item to that hospital (h), then the supplier (s) will also be supplying the required item (i) to the hospital (h). In this example, assume that a description of an item (itemDescription) uniquely identifies each type of item.
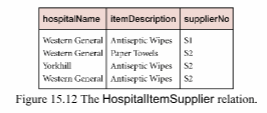
(a) Describe why the relation shown in Figure 15.12 is not in 5NF.
(b) Describe and illustrate the process of normalizing the relation shown in Figure 15.12 to 5NF.
When working with two-dimensional arrays, the length field holds the number of rows in an array and each row has a length field that holds the number of columns in the row.
Answer the following statement true (T) or false (F)
A _____ node is the text contained within an element.
A. ?text B. ?comment C. ?content D. ?string
Which of the following is used to ensure that only humans obtain free email accounts?
a. Atomicity, consistency, isolation, and durability (ACID) b. Microprocessor without Interlocked Pipeline Stages (MIPS) c. Completely Automated Public Turing Test to Tell Computers and Humans Apart (CAPTCHA) d. Document Style Semantics and Specification Language (DSSSL)