Jane, an administrator, is primarily concerned with blocking external attackers from gaining information on remote employees by scanning their laptops. Which of the following security applications is BEST suited for this task?
A. Host IDS
B. Personal firewall
C. Anti-spam software
D. Anti-virus software
Answer: B. Personal firewall
You might also like to view...
Which of the following describes the primary reason that one would override a property or method?
a. the property or method in the base class was declared as Private and can’t be used b. the property or method in the base class has an error c. the property or method in the base class is not appropriate for the derived class d. the property or method does not exist in the base class
Expand the acronym WAN.
What will be an ideal response?
?In the accompanying figure of a PowerPoint 2016 presentation, box _____ is pointing to the Decrease Font Size button.
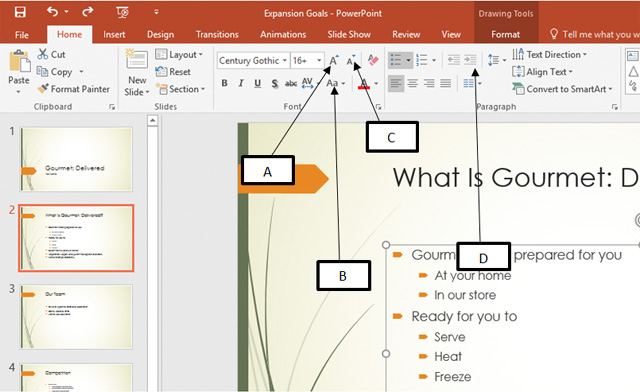
A. ?C B. ?B C. ?D D. ?A
isLetter(str) is a string manipulation function.
Answer the following statement true (T) or false (F)