The specification of a file's location is called a(n) ____________________.
Fill in the blank(s) with the appropriate word(s).
path
Computer Science & Information Technology
You might also like to view...
Consider a polynomial kernel of degree K defined in graph frequency domain as
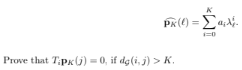
Computer Science & Information Technology
Most organizations that have trademarks attempt to protect these secrets using nondisclosure agreements (NDAs)
Indicate whether the statement is true or false.
Computer Science & Information Technology
Fuzz testing and reliability testing are conducted during system testing.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
Autonomous Systems communicate with each other using a(n) _______________ protocol.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology