Trust and authentication generally have an inverse relationship
a. true
b. false
Answer: a. true
You might also like to view...
Assume that, in the anonymous electronic cash protocol, the bank is honest but the customer and the merchant might not be.
a. After receiving the tokens from the bank, the customer later claims that she never received them. Explain what the bank should then do and why it is correct. b. After receiving the message containing the purchase order and the tokens from the customer, the merchant claims never to have received the message. Explain what the customer should do and why.
____ work(s) in Apple devices such as the iPhone and iPad.
A. TrueType Fonts B. Embedded OpenType fonts C. Web Open Font Format D. SVG fonts
When an image imported on a Macintosh is viewed on a PC, it appears:
a. darker and richer because the values have changed. b. lighter and less saturated because the values have changed. c. darker and richer even though the values have not changed. d. lighter and less saturated even though the values have not changed. e. exactly the same.
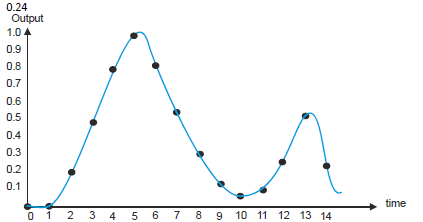
Consider the waveform below. If it were applied to a simple DSP with the transfer function yi = 0.7xi + 0.3xi?1, what would the output look like? Assume the data is 0.0 0.0 0.2 0.5 0.8 1.0 0.85 0.55 0.3 0.15 0.05 0.1 0.25 0.5