The term ____________________ refers to any program or set of program instructions designed to surreptitiously enter a computer, disrupt its normal operations, or gather sensitive data.
Fill in the blank(s) with the appropriate word(s).
malicious code
Computer Science & Information Technology
You might also like to view...
Discuss the aim of the application and system security function.
What will be an ideal response?
Computer Science & Information Technology
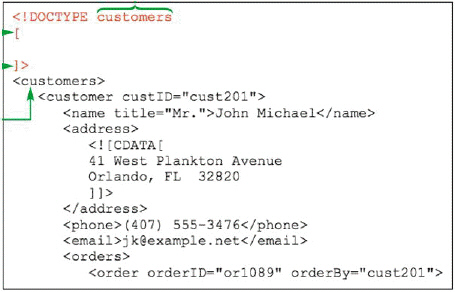 The DOCTYPE declaration has to be added to a document epilog as shown in the accompanying figure.
The DOCTYPE declaration has to be added to a document epilog as shown in the accompanying figure.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
________ uses multiple processors, or multi-core processors, to share processing tasks
A) Distributed processing B) Parallel processing C) Pipelining D) Serial processing
Computer Science & Information Technology
Which of the following partitions contains the original image of the operating system?
a. Primary b. Extended c. Factory Recovery Partition d. Recovery e. Logical
Computer Science & Information Technology