Which of the following best practices is commonly found at the end of router ACLs?
A. Time of day restrictions
B. Implicit deny
C. Implicit allow
D. Role-based access controls
Answer: B. Implicit deny
Computer Science & Information Technology
You might also like to view...
Java allows small programs, called _____, to be embedded with an Hypertext Markup Language (HTML) document.
A. cookies B. subroutines C. applets D. packets
Computer Science & Information Technology
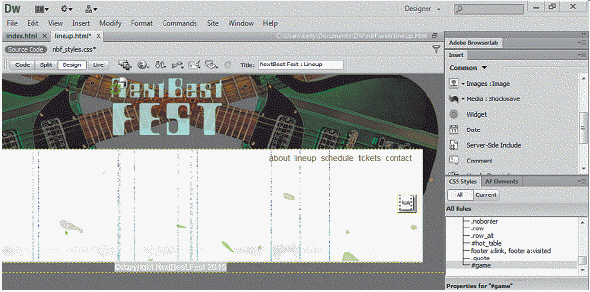 The extension of the file in the accompanying figure is ____.
The extension of the file in the accompanying figure is ____.
A. .dir B. .dxr C. .cxt D. .dcr
Computer Science & Information Technology
When business logic requires the comparison of two or more fields, you need to use a(n) ________ macro
Fill in the blank(s) with correct word
Computer Science & Information Technology
The ________ window has options to create multiple PivotCharts on the same worksheet using data from all connected data sources
A) PivotChart B) Power Pivot C) PivotTable D) Power View
Computer Science & Information Technology