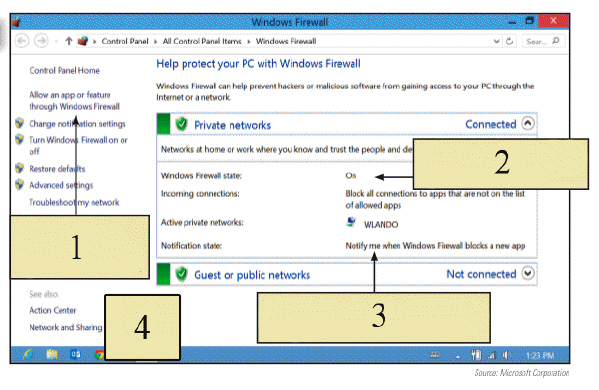
 In the figure above, the icon represented by item 2 means the computer ____.
In the figure above, the icon represented by item 2 means the computer ____.
A. has the Windows Firewall enabled
B. is powered off
C. is in standby mode
D. cannot connect to an Ethernet network
Answer: A
You might also like to view...
You can select a word by using the ____ key(s).
A. OPTION-SHIFT-RIGHT ARROW B. COMMAND-A C. SHIFT-LEFT ARROW D. COMMAND-W
The ________ appears after adding a grouping to a form or report
A) Group Footer B) Page Header C) Page Footer D) Group Header
In the ArrayBag class, what function does the __str__ method use to generate a sequence of strings from a bag?
A. count B. len C. add D. map
___________is the potential for the function of a biometric system to be compromised by fraudulent activity, design flaw, accident, hardware failure, or external environmental condition.
A. data vaulting B. accuracy C. backups D. vulnerability E. compromise