Using an encrypted tunnel between a computer (or remote network) and a private network is an example of using this type of network.
A. peer-to-peer
B. client/server
C. dial-up
D. virtual private network (VPN)
Answer: D
Computer Science & Information Technology
You might also like to view...
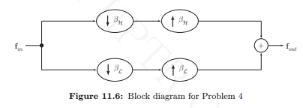
Consider the same graph as in Problem 3 if the output signal to the block diagram shown in Figure 11.6 is fout = [ ? 2 , ? 1 , 3 , 9 , 0 , 0] T . Compute the input signal fin
Computer Science & Information Technology
Pictures are always resized proportionally regardless of which of the sizing handles you use
Indicate whether the statement is true or false
Computer Science & Information Technology
Describe factors that affect wireless network speeds.
What will be an ideal response?
Computer Science & Information Technology
Software risk impact assessment should focus on consequences affecting
A. business, technology, process B. marketability, cost, personnel C. performance, support, cost, schedule D. planning, resources, cost, schedule
Computer Science & Information Technology