Discuss the similarities to different patterns used in software engineering. Which pattern fits best?
Adapter pattern – Modelling
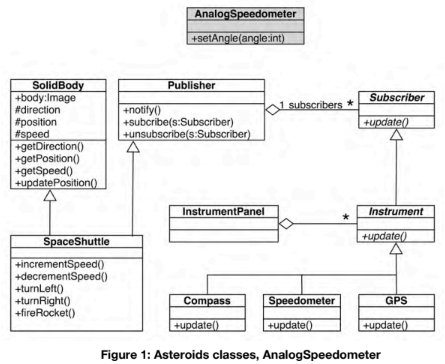
A new instrument (AnalogSpeedometer) from a legacy system has to be integrated into
Asteroids (see Figure 1). The existing class AnalogSpeedometer must not be changed.
Therefore an Adapter pattern should be used. Integrate the AnalogSpeedometer into the
existing model.
2) Pattern abstraction

3) Dynamical model
Model the dynamical behaviour of incrementing the speed in a sequence diagram.
Consider the following classes and actors:
AnalogSpeedometer, SpaceShuttleController, “the adapter”, SpaceShuttle, User.
4) Adapter pattern (programming assignment)
Integrate the AnalogSpeedometer by applying the adapter pattern without modifying it
and with minimal modifications to other classes.
IMPORTANT – Submission Requirements for programming assignment:
Warning: Due to the large number of students, it is very important to exactly fulfill the
submission requirements. Otherwise your submission cannot be processed.
• Only code compiling without any errors will be accepted. Do not submit non-
compiling code!
• Use Java 1.5 and the supplied ANT script to compile
• To submit your solution, execute the ANT target “zip”. When prompted to do so
enter your exercise group and the last name of all of your team members.
• Please double check the generated “zip” file in the asteroids directory:
o It should be named following the schema
o Unzip once and check the contents: src-folder und jar-Archiv
• In your email...
o ...choose the name of the zip archive as subject
o ...note the complete name and “Matrikelnummer” of all team members
• Send the email to your tutor only
You might also like to view...
Give a command to
a. Redirect standard output from a sort command to a file named phone_list. Assume the input file is named numbers. b. Translate all occurrences of the characters [ and { to the character (, and all occurrences of the characters ] and } to the character ), in the file permdemos.c. c. Create a file named book that contains the contents of two other files: part1 and part2.
When you say that software is of high quality, what do you mean? How does security fit in your definition of quality? For example, can an application be insecure and still be "good"?
What will be an ideal response?
The summary of changes in the Reviewing Pane shows only insertions and deletions.
Answer the following statement true (T) or false (F)
Anti-malware programs can operate as ____________________ that passively monitor a computer's activity, checking for viruses only when certain events occur, such as a program executing or a file being downloaded.
Fill in the blank(s) with the appropriate word(s).