Commercial encryption systems are constantly being researched by cryptologists to ensure that the systems are not vulnerable to a_______ attack.
a) hacker.
b) cipher.
c) cryptanalytic.
d) None of the above.
c) cryptanalytic.
You might also like to view...
Write a code fragment that prints every other character in a String object called word starting with the first character.
What will be an ideal response?
String sentence;String str1, str2, str3, str4;int length1;sentence = "First exam is on Monday.";str1 = sentence.substring(6, 12);str2 = str1.substring(0, 4);str3 = sentence.replace('i', '#');str4 = sentence.indexOf("on");length1 = sentence.length();Based on the code above, what is the value of str1?
A. exam i B. exam C. exam is D. on Monday
?
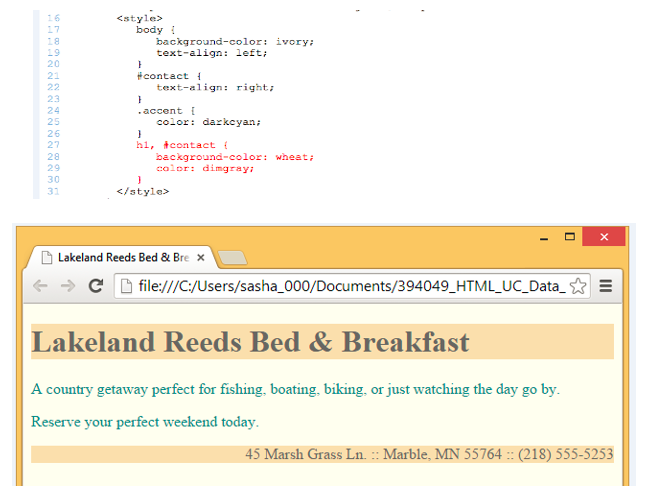
Fill in the blank(s) with the appropriate word(s).
RAID level ________ has the highest disk overhead of all RAID types.
A. 0 B. 1 C. 3 D. 5