a code used to identify and authenticate a person or organization sending data over a network
adware
digital certificate
grayware
keylogger
dictionary attack
social engineering
tailgating
Trojan
zombie
worm
digital certificate
Computer Science & Information Technology
You might also like to view...
Which method call converts the value in variable stringVariable to an integer?
a. Convert.toInt(stringVariable) b. Convert.parseInt(stringVariable) c. Integer.parseInt(stringVariable) d. Integer.toInt(stringVariable)
Computer Science & Information Technology
Which of the following is NOT a problem that may result from allowing uncontrolled access to the database?
A. dirty reads B. lost updates C. concurrency control D. incorrect summary
Computer Science & Information Technology
A Bluetooth network is called a(n) ____________________.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
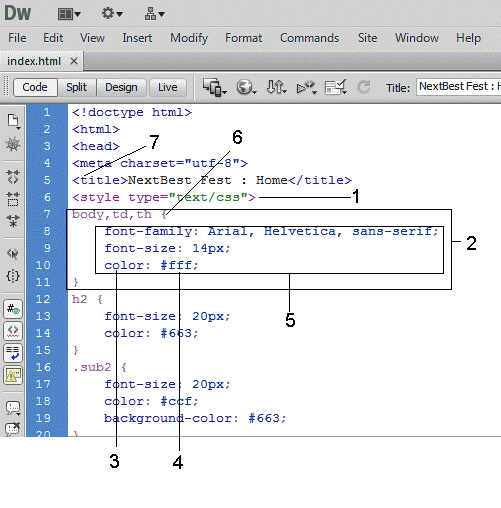 The item marked ____ in the accompanying figure is an attribute value.
The item marked ____ in the accompanying figure is an attribute value.
A. 1 B. 3 C. 4 D. 6
Computer Science & Information Technology