In a Word table, the intersection of a row and a column is called a(n) ____________________, and is filled with text.
Fill in the blank(s) with the appropriate word(s).
cell
Computer Science & Information Technology
You might also like to view...
Write a SELECT statement to list course data sorted by course number.
What will be an ideal response?
Computer Science & Information Technology
Blacklists and whitelists are most commonly used in ____ detection and stateful protocol analysis.
A. blacklist B. signature-based C. statistical anomaly-based D. behavior-based
Computer Science & Information Technology
FIGURE 11-1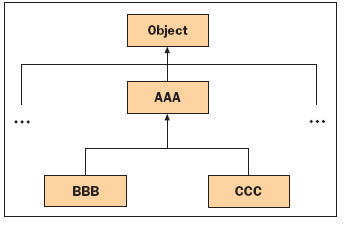 Figure 11-1 above shows an example of a ____ hierarchy.
Figure 11-1 above shows an example of a ____ hierarchy.
A. class B. interface C. program D. method
Computer Science & Information Technology
In troubleshooting, if a theory is not confirmed, re-establish a new theory or __________.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology