If a user is created without a password and the domain's password policy requires a non-blank password, what is the result?
What will be an ideal response?
The user account is created, but automatically disabled.
You might also like to view...
Match each term with the correct statement below.
A. used to test the voltage on a network cable. B. device that works in promiscuous mode to capture detailed information about the traffic moving across a network, including protocol and OSI layer information. C. can be used to verify that a DNS is server is online and working. D. can be used to monitor server components such as hard disks, memory, and the processor. E. can detect many forms of network traffic and capture packets and frames for analysis F. provides network management services through agents and management systems. G. backs up all files, files that have changed by date, or files that have changed after the previous backup. H. used by Performance Monitor when there are two or more types of elements to monitor such as two or more NICs or disk drives I. a specific situation or event detected by SNMP that a network administrator may want to be warned about
Limiting the club members in a data source to only those who live in area code 14072 is an example of ________
A) filtering B) sorting C) merging D) sifting
The Share Workbook dialog box in a shared workbook shows ____.
A. a list of people currently using the workbook B. only the name of the computer user C. all user comments and changes D. the change history
Write the equation of the line pictured in the graph.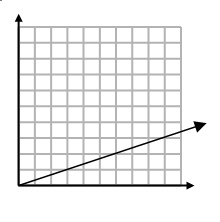
What will be an ideal response?