Digits, letters and special symbols are referred to as_________ .
a) constants
b) ints
c) Strings
d) characters
d) characters
You might also like to view...
Which of the following is the most common web application security flaw?
A) Failure to validate output B) Failure to validate input C) Dynamic data validation D) Static data validation
Which IPv6 header includes fields for the intermediary addresses through which the IPv6 packet should be forwarded?
A. Routing extension B. Destination Options C. Hop-by-Hop Options D. Fragment extension
Press the ________ to complete the process of entering a formula.
a. Enter key b. down arrow c. tab d. spacebar
Determine whether the graphs of the equations are parallel, perpendicular, or neither.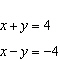
What will be an ideal response?