An interface and all of its method headings are normally declared to be:
(a) public
(b) private
(c) protected
(d) package access
(a) public
You might also like to view...
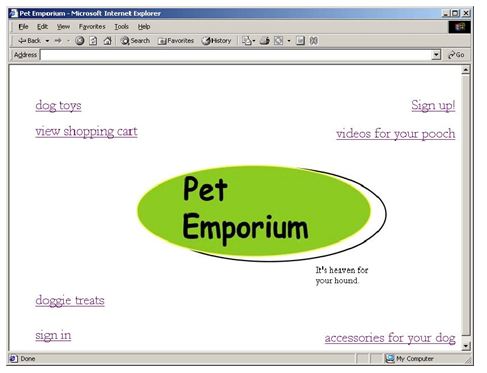
The following is a proposed home page for a Web site about pets.
a. Which of the link names are most closely related? Organize them into two groups according to the meaning of the link names and list the groups. Explain your rationale for the groups.
b. What ways do you know to organize information visually? List all five of them. For each one, decide if it would be useful to when reorganizing the link names on the Web site. Explain your answers.
c. Make a photocopy of the home page, cut it apart using scissors and make a new version of the page where the related links appear to be part of a group.
Answer the following statements true (T) or false (F)
1. A pattern that contains symbols that represent the type of data that must be present in a field is called a regular expression . 2. XML documents may be validated by comparing them to a DTD or a schema. 3. In an eCommerce system, data is generally entered into the system by the programmer. 4. Data entered at the point of sale are reused throughout the entire order fulfillment process in a(n) ecommerce system. 5. Accuracy is improved by better feedback. 6. Ensuring the quality of the data input to the information system is critical to ensuring quality output.
Click the ________ tab to begin a Word outline
A) Home B) Page Layout C) File D) Insert
Match each item with a statement below.
A. Windows 7 uses these to identify computers on a network that are not part of a domain B. Windows software that enables your computer to access shared resources on other Windows computers C. automatic address assignment when no DHCP server is available D. associates users of UNIX systems who have common access needs. E. a subnetwork technology used for SANS and enables gigabit speed data transfers F. special set of permissions that may be associated with executable programs running in UNIX/Linux systems. G. a device with software that manages shared printing on a network. H. enables you to turn one computer on your network into an "Internet server." I. resources are made available through a third-party outsourcer, but are accessible only to users within a specific organization.