Conduct a Search of Recent Malware
Malware, or malicious software, refers to a variety of malicious software programs that can be used
to cause harm to computer systems, steal data, and bypass security measures. Malware can also attack
critical infrastructure, disable emergency services, cause assembly lines to make defective products,
disable electric generators, and disrupt transportation services. Security experts estimate that more
than one million new malware threats are released each day. A McAfee Labs report indicates almost
500 million known malware threats at the end of 2015.
Note: You can use the web browser in the virtual machine installed in a previous lab to research security related issues. By using the virtual machine, you may prevent malware from being installed on your computer.
a. Using your favorite search engine, conduct a search for recent malware. During your
search, choose four examples of malware, each one from a different malware type,
and be prepared to discuss details on what each does, how each is transmitted and the
impact each causes.
Examples of malware types include: Trojan, Hoax, Adware, Malware, PUP, Exploit, and
Vulnerability. Some suggested websites to search malware are listed below:
McAfee
Malwarebytes
Security Week
TechNewsWorld
b. Read the information about the malware found from your search in step 1a, choose one
and write a short summary that explains what the malware does, how it is transmitted,
and the impact it causes.
You might also like to view...
Given the C++ output statements. What is the output of these lines of code? Explain. cout << "If you have "; cout << "a number of pods "; cout << "you can quit."; cout << "\n";
What will be an ideal response?
To create a crosstab query using fields from more than one table, the user must create a select query with the fields from both tables and then use the query as the data source for the crosstab query
Indicate whether the statement is true or false
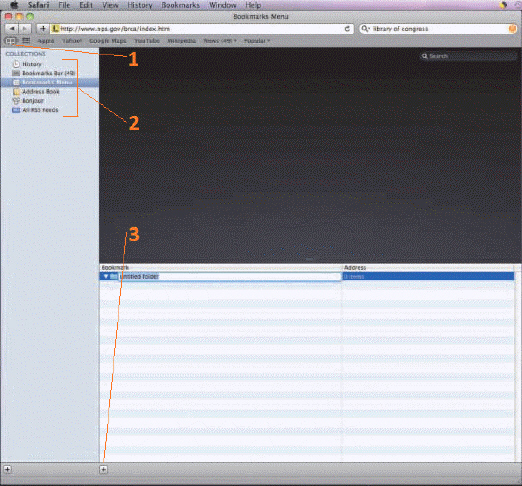 In the accompanying figure, which illustrates a new folder added to the Bookmarks Menu, Item 3 indicates the ____.
In the accompanying figure, which illustrates a new folder added to the Bookmarks Menu, Item 3 indicates the ____.
A. Add button B. Create a bookmarks folder button C. Close button D. Show all bookmarks button
On the Column Display page of the LOV Wizard, the ______ column specifies the form text item to which the LOV transfers the user's LOV selection for the current field.
Fill in the blank(s) with the appropriate word(s).