An administrator would like to search for network vulnerabilities on servers, routers, and embedded appliances. Which of the following tools would MOST likely accomplish this?
A. Baseline analyzer
B. Ping
C. Protocol analyzer
D. Nessus
Ans: D. Nessus
You might also like to view...
Which of the following is not a fundamental requirement of a successful, secure transaction?
(a) Privacy. (b) Cryptography. (c) Integrity. (d) Non-repudiation
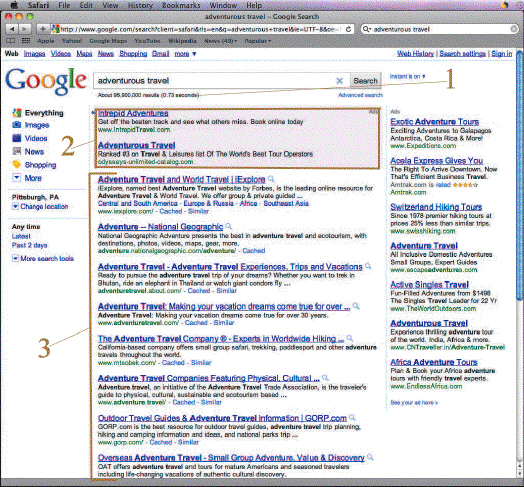 In the accompanying figure, Item 3 indicates the ____ on a Google search results page.
In the accompanying figure, Item 3 indicates the ____ on a Google search results page.
A. sponsored links or ads B. number of hits C. search results D. search fields
Case 2The InDesign layout is ready to share with your client. Answer the following questions about making an InDesign layout available on the web. Which of the following is a feature in InDesign that you can use to do a quality-control check before uploading your InDesign document to a website?
A. The Package feature B. The Hosting Management feature C. The Quick Check feature D. The Check It Out feature
USB flash drives (sometimes called USB flash memory drives, ____ drives, or jump drives) consist of flash memory media integrated into a self-contained unit that connects to a computer or other device via a standard USB port and is powered via the USB port.
A. half B. thumb C. finger D. hand