In US v. John Doe, evidence was thrown out of court because the defendant had been forced to reveal the password for an encrypted drive against his will. The judge in this case ruled that the defendant's right under ______________________ had been violated
a. The Fourth Amendment
b. The First Amendment.
c. The Second Amendment
d. The Fifth Amendment
d.
Computer Science & Information Technology
You might also like to view...
Data produced by a computer is sent to a(n) ____________, which formats and presents it.
a. input device b. output device c. storage device d. program
Computer Science & Information Technology
________ is a technique where the underlying operating environment of an application is virtualized.
A) Container virtualization B) Traffic engineering C) CCN D) COTS
Computer Science & Information Technology
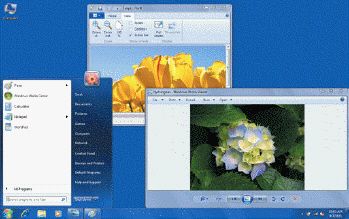 As a consumer, you can choose from any of the following editions of the operating system shown in the accompanying figure EXCEPT ____.
As a consumer, you can choose from any of the following editions of the operating system shown in the accompanying figure EXCEPT ____.
A. Premium B. Professional C. Basic D. Ultimate
Computer Science & Information Technology
Define a mail transfer agent (MTA) and provide an example.
What will be an ideal response?
Computer Science & Information Technology