Match the following tools with their uses
1. The most notable early hacking group a. Plovernet
2. One of the first hacking boards, popular on the West Coast b. Legion of Doom
3. East Coast hacking board that became a breeding ground for hacking groups c. ALTOS
4. The epitome of sophisticated international hacking, originally formed in Germany d. 414 Private
5. Group of teenage hackers who hacked into the Los Alamos military computers in the early 1980s e. 8BBS
Answer: 1. b
2. e
3. a
4. c
5. d
You might also like to view...
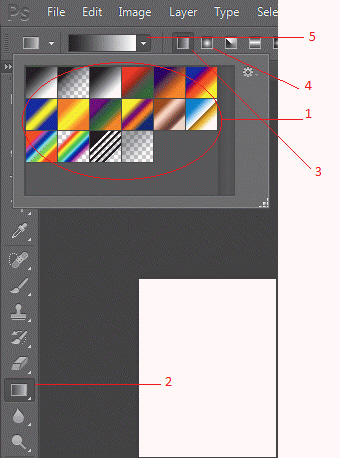 In the accompanying figure, item 1 points to the ____.
In the accompanying figure, item 1 points to the ____.
A. radial gradient B. default gradient swatches C. linear gradient D. gradient tool
Two or more tables that contain duplicate data are an example of:
A) one-to-many relationships. B) data redundancy. C) many-to-many relationships. D) data backup.
The depth first traversal is similar to the preorder traversal of a binary tree.
Answer the following statement true (T) or false (F)
What element property would you use when copying the contents of one text field to another text field??
A. ?value B. ?default C. ?content D. ?selectedIndex