Social engineering is composed of a variety of methods to manipulate users into performing actions or providing information. Which of the following are among the many methods used during social engineering?
a. Pretexting
b. Phishing
c. Baiting
d. All answers provided are correct.
D. Among the many methods used during a social engineering attack, the most common are pretexting, phishing, Trojan horse, and baiting.
Computer Science & Information Technology
You might also like to view...
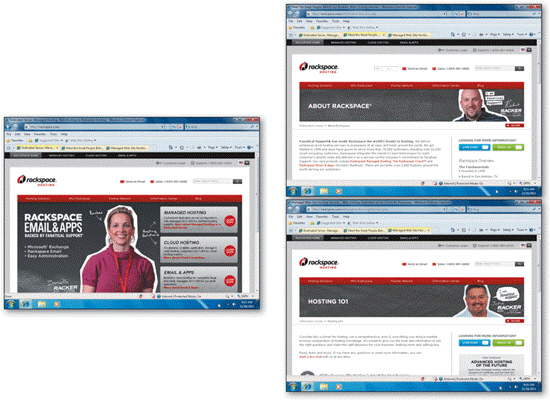 The consistent application of _________________________ and repeating content elements across all the pages at a site unifies its look and feel, as shown in the accompanying figure.
The consistent application of _________________________ and repeating content elements across all the pages at a site unifies its look and feel, as shown in the accompanying figure.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
Describe the Session Layer of the OSI model.
What will be an ideal response?
Computer Science & Information Technology
Provide the steps in the start-up process.
What will be an ideal response?
Computer Science & Information Technology
What are YaST groups? List the names of available YaST groups
What will be an ideal response?
Computer Science & Information Technology