____ measures image clarity.
A. Pixel size
B. Resolution
C. Bit depth
D. Dot pitch
Answer: D
You might also like to view...
Create a Cash Register application (Fig. 11.23) with a numeric keypad similar to that in the Security Panel application you built in this tutorial. In addition to numbers, the cash register includes a decimal point JButton. Also, there are Enter, Total, Delete and Clear JButtons. These JButtons add an amount to the subtotal, cal- culate the tax and total, delete the current amount in the $ JTextField (in case the user makes an error during input) and clear the current amounts displayed, respectively. You will implement the methods for the Enter and Total JButtons. Assume the user enters positive, non-zero amounts. Sales tax should be calculated on the amount purchased using a switch statement. Add the tax amount to the subtotal to calculate the total. Display the
Amounts under $100 = 5% (.05) sales tax
Amounts between $100 and $499 = 7.5% (.075) sales tax
Amounts $500 and over = 10% (.10) sales tax
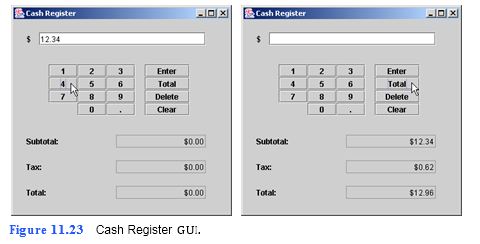
a) Copying the template to your working directory. Copy the directory C:Examples Tutorial11ExercisesCashRegister to your C:SimplyJava directory.
b) Opening the template file. Open the CashRegister.java file in your text editor.
c) Adding code to the enterJButtonActionPerformed method. In the enter- JButtonActionPerformed method (lines 496–499 in the template code), insert a statement that converts the value in amountJTextField to type double and adds the value to instance variable subtotal. Using the DecimalFormat variable dollars (created in line 56), insert a statement that formats the new value of subtotal and
displays it in subtotalJTextField. Insert a statement that clears the amountJText- Field (so the user can enter the next amount).
d) Determining the tax rate. In the totalJButtonActionPerformed meth
Which tools are tunneling protocols?
A. PPTP and L2TP B. OpenVPN and IPsec C. IPSec and Radius D. HTTP and HTTPS
Civil liberty organizations have voiced concerns that should be addressed regarding the use of biometric devices before any widespread deployment. These major areas of concern include:
A. storage, vulnerability B. confidence, authenticity C. linking, ubiquity D. all of the above E. none of the above
A vSphere Administrator just finished installing new software on the Windows vCenter Server and notices that vCenter Server services no longer start properly. What two tasks should be done next? (Choose two.)
A. Contact the server hardware manufacturer. B. Check for network port conflicts. C. Reinstall vCenter Server. D. Check the vCenter Server logs.