An attacker controlling bots in a coordinated attack against a victim is known as a ________.
A. DDoS attack
B. HTTP attack
C. DoS attack
D. Firewall attack
A. DDoS attack
Computer Science & Information Technology
You might also like to view...
Member functions _________ and __________ of istream and ostream set the file-position pointer to a specific location in an input or output stream, respectively.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
Create an applet that will display the following logo in its upper left corner. Hint: Draw the logo in the paint method, but remember to call super.paint().
What will be an ideal response?
Computer Science & Information Technology
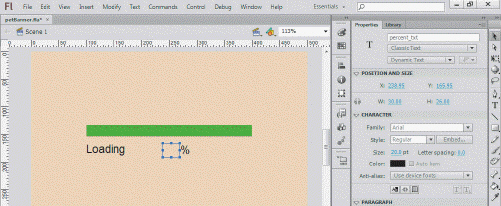 In the figure above, the Character setting section of the Property inspector is showing the settings for the ____.
In the figure above, the Character setting section of the Property inspector is showing the settings for the ____.
A. stage B. user's screen C. text block D. green bar
Computer Science & Information Technology
The template that serves as a basis for all Word documents is the:
What will be an ideal response?
Computer Science & Information Technology