To guard against data theft, most cell networks use data ____.?
A. ?encryption
B. ?ports
C. ?modems
D. ?cables
Answer: A
Computer Science & Information Technology
You might also like to view...
Task dependencies in Project can be entered in minutes, hours, days, weeks, months, and years
Indicate whether the statement is true or false
Computer Science & Information Technology
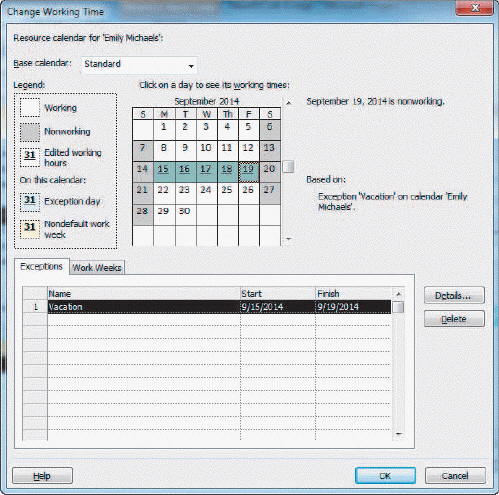 The resource calendar for Emily Michaels in the accompanying figure is based on the _____________ calendar.
The resource calendar for Emily Michaels in the accompanying figure is based on the _____________ calendar.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
When you use the VLOOKUP function, the ________ column in the array is used to look up the value.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
The decimal equivalent for 3.42e-5 in scientific notation is .00342.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology