An Alice world is created by placing items in the world. These items are called ___________________.
Fill in the blank(s) with the appropriate word(s).
ANSWER: objects
You might also like to view...
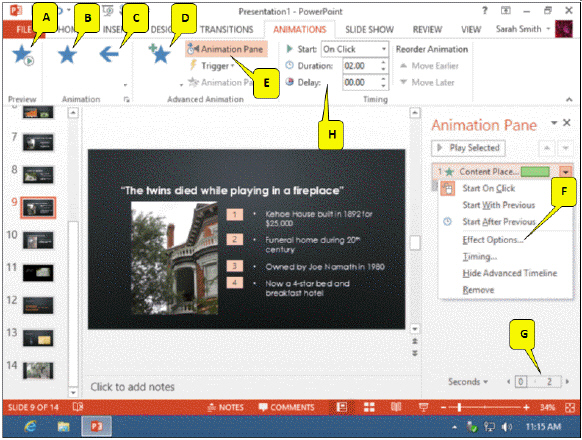 Referring to the figure above, which callout points to the control used to specify the direction of the animation?
Referring to the figure above, which callout points to the control used to specify the direction of the animation?
A. A B. B C. C D. H
____________ can occur when a company’s wireless LAN or wireless access points to wired LANs in close proximity and may create overlapping transmission ranges. A user intending to connect to one LAN may unintentionally lock on to a wireless access point from a neighboring network.
A. Network injection B. Denial of service attacks C. Man-in-the-middle attacks D. Accidental association
What are the advantages of calculating totals in a table total row?
What will be an ideal response?
Describe the system partition.
What will be an ideal response?