The ____ cipher rearranges the values within a block to create the ciphertext.
A. transposition
B. polyalphabetic substitution
C. Vernam
D. monoalphabetic substitution
Answer: A
Computer Science & Information Technology
You might also like to view...
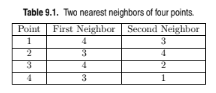
Table 9.1 lists the two nearest neighbors of four points.
Computer Science & Information Technology
What is the term used when an IDPS doesn't recognize that an attack is underway?
A. false negative B. true positive C. negative activity D. positive signature
Computer Science & Information Technology
C# apps begin execution at method _________.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
The ________ area includes the chart and all of its elements
Fill in the blank(s) with correct word
Computer Science & Information Technology