________ is a lossy image format
A) MP3
B) TIFF
C) PDF
D) JPEG
D
Computer Science & Information Technology
You might also like to view...
Use the _______ method of the ArrayList class to generate an Iterator.
a) getIterator b) makeIterator c) iterator d) iterate
Computer Science & Information Technology
A power surge is often referred to as a ____.
A. brown-out B. black-out C. dim D. spike
Computer Science & Information Technology
A spam __________ uses a set of rules to examine email messages and determine which are spam.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
Find an equation of a line given the following information. The final answer should be left in slope-intercept form. Passes through the points 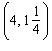 and
and ![]()
What will be an ideal response?
Computer Science & Information Technology