One method of heuristic analysis allows the suspicious file to run in a guarded environment called a(n) ___________.
Fill in the blank(s) with the appropriate word(s).
sandbox
Computer Science & Information Technology
You might also like to view...
A variable of the ____________ data type can hold any sequence of characters, such as a person’s name, address, or password.
a. int b. double c. string d. decimal
Computer Science & Information Technology
A ___________ statement encloses code that may raise an exception.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
Which CentOS 7 file and directory permission provides read and execute authority?
A. r-x B. r-- C. --x D. ---
Computer Science & Information Technology
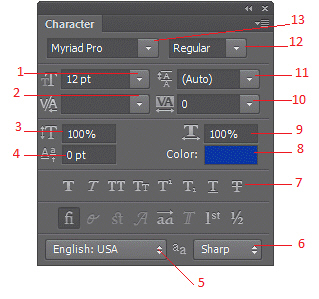 In the accompanying figure, item 3 points to the ____.
In the accompanying figure, item 3 points to the ____.
A. Kerning B. Horizontal scale C. Vertical scale D. Baseline shift
Computer Science & Information Technology