Background 1 is a code used by Access to represent the color ________
A) black
B) red
C) white
D) blue
C
You might also like to view...
A video can be played by pressing ________
A) [F3] B) [Alt]+[P] C) [Ctrl]+[P] D) [Shift]+[P]
Which IPv6 ACL statement would be used to allow all SMTP traffic coming from the 2001:db8:db23:ad34::/64 network to the 2001:db8:bde1:db34::/64 network?
A) allow tcp 2001:db8:db23:ad34::/64 2001:db8:bde1:db34::/64 eq 161 B) permit tcp 2001:db8:db23:ad34::/64 2001:db8:bde1:db34::/64 eq 25 C) permit udp 2001:db8:db23:ad34::/64 2001:db8:bde1:db34::/64 eq 161 D) allow udp 2001:db8:db23:ad34::/64 2001:db8:bde1:db34::/64 eq 25
Fonts can be altered further with all of these EXCEPT HTML and CSS ____.
A. backgrounds B. styles C. attributes D. values
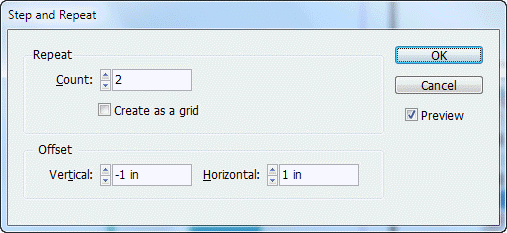
A. to the right and up B. to the right and down C. to the left and up D. to the left and down