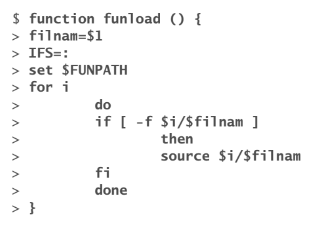
Write a function named funload that takes as its single argument the name of a file containing other functions. The purpose of funload is to make all functions in the named file available in the current shell; that is, funload loads the functions from the named file. To locate the file, funload searches the colon-separated list of directories given by the environment variable FUNPATH. Assume the format of FUNPATH is the same as PATH and the search of FUNPATH is similar to the shell’s search of the PATH variable.
What will be an ideal response?
You might also like to view...
The AddTimeMarker method is used in conjunction with ________.
a) the window.SetTimer method b) JavaScript event handling c) the ActiveX-timer array d) the revealTrans filter
For watching HD streaming video for an hour, the approximate data usage is 3-6 MB.
Answer the following statement true (T) or false (F)
What type of software can be installed in an individual's web browser to prevent ads from displaying?
A. antivirus B. ad blocking C. cookie scanning D. ad sensing
In both direct flooding attacks and ______ the use of spoofed source addresses results in response packets being scattered across the Internet and thus detectable.
A. SYN spoofing attacks B. indirect flooding attacks C. ICMP attacks D. system address spoofing