Connection-oriented, iterative server.
Using the three-tier software architecture presented in this chapter, design and implement a client-server suite for the following protocol (it is not a well-known service): Each client sends to the server a name. The server accumulates the names received from successive clients (by appending each, with a linefeed (‘
’), to a static string). Upon receiving a name, the server sends the names that it has collected to the client. The figure below illustrates the sequence diagram of a session of the protocol.
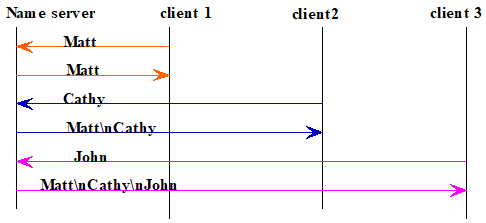
Model the suite after the Echo*2 suite. The client sends one line only, but will need to read multiple lines, using syntax as follows:
```
public String getNames( String message) throws
SocketException, IOException {
String names = "", nextName = "";;
mySocket.sendMessage( message);
// now receive the names
nextName = mySocket.receiveMessage( );
while (nextName != null) {
names += nextName;
nextName = mySocket.receiveMessage( );
}
return names;
} //end getNames
```
The server accumulates the names in a string, in a manner similar to the description for (i).
You might also like to view...
Outline the main difference between TLS and XML security. Explain why XML is particularly suitable for the role it plays, in terms of these differences.
What will be an ideal response?
What can be set up to run with real-time protection that will alert you when malicious programs attempt to install on your computer?
A) Windows Firewall B) Windows Help C) Windows Updates D) Windows Defender
The Millers are empty nesters and no longer need a four-bedroom house. They have scheduled a meeting with a realtor. In preparation, they are doing an inventory of their home. They have opened a Microsoft Word file to begin documenting what they have. The Millers insert a 9-column-by-4-row table in their Word file, with each column representing a room in their house.Before printing their table, the Millers add black grid lines to outline each cell in the table by selecting ____ after clicking the Borders button in the Draw Borders group.
A. Horizontal B. Vertical C. Inside D. All
Which of the following is not an additional preparatory task for a Windows 7 upgrade?
a. Check for BIOS upgrades. b. Reset the IP address. c. Scan and eliminate viruses. d. Install any upgrade packs to make older applications compatible with Windows 7.