Perhaps the most widely used public-key algorithms are _________ and Diffie-Hellman.
Fill in the blank(s) with the appropriate word(s).
MD5
Computer Science & Information Technology
You might also like to view...
An example of a container is a/an:
a. array b. vector c. linked list d. all of the above
Computer Science & Information Technology
How can you trick make into rebuilding all modules of your program?
What will be an ideal response?
Computer Science & Information Technology
Maintenance alerts cover information related to system maintenance like problem reports, file history, and drive status
Indicate whether the statement is true or false
Computer Science & Information Technology
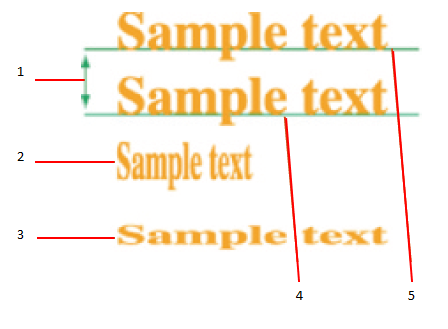
Answer the following statement true (T) or false (F)
Computer Science & Information Technology