Which facet of securing access to network data makes data unusable to anyone except authorized users?
A. encryption
B. authentication
C. malware protection
D. security devices
Answer: A
You might also like to view...
Use the Zoom control to see the entire page.
Answer the following statement true (T) or false (F)
________ are embedded in an image on the screen.
(a) Cookies. (b) ID cards. (c) Click-through advertisements. (d) Web bugs.
In Tutorial 15, your Lottery Picker application selected numbers for four different types of lotteries. In this exercise, you enhance the Lottery Picker to select four different sets of number for the five-number lottery and to pre- vent duplicate numbers from being selected (Fig. 17.34). Recall that the lottery is played as follows:
? Five-number lotteries require players to choose five unique numbers in the range of 0–39. 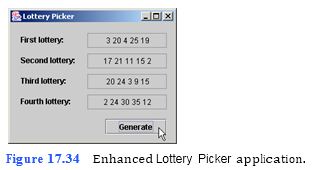
a) Copying the template to your work directory. Copy the C:ExamplesTutorial17 ExercisesEnhancedLotteryPicker directory to your C:SimplyJava directory.
b) Opening the template file. Open the LotteryPicker.java file in your text editor.
c) Iterating over the four lotteries. Add code on line 138 to begin a for statement in your application which will execute four times—once for each lottery. Use variable lottery as the for statement’s counter.
d) Initialize the boolean array. To generate unique numbers in each lottery, you will use a two-dimensional boolean array, uniqueNumber (declared for you in the tem- plate). When a number has been selected for a lottery, the value of that variable in the array (indexed by the lottery and the number selected) will be true. First, you must initialize the value for the lottery’s numbers to false. Add a nested for state-
ment to set the
The increased use of which of the following is argued as evidence of the U.S. Patriot Act's potential danger?
a. Omnibus Crime Control and Safe Streets Act b. Foreign Intelligence Surveillance Act c. Federal Rules of Civil Procedure d. National Security Letters