If you want to perform a TCP stealth scan, which of the following commands you should use?
a. nmap –sT 192.168.1.108
b. nmap –sS 192.168.1.108
c. nmap -sU 192.168.1.108
d. nmap –sI 192.168.1.108
ANS: B
You might also like to view...
Write the header for a loop that will process each character of the string object movie in turn.
What will be an ideal response?
It is important to maintain an attitude of humility when doing agile modeling.
What will be an ideal response?
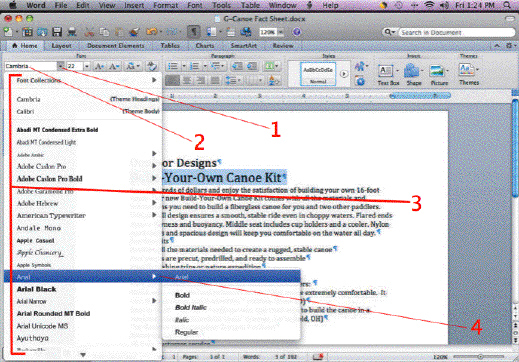 In the accompanying figure, Item 4 points to the ____.
In the accompanying figure, Item 4 points to the ____.
A. disclosure triangle B. Font Size pop-up menu arrow C. Font pop-up menu arrow D. Font group pop-up menu arrow
Using ________ allows you to indicate an animation should begin either on the click of the mouse, at the same time as the previous animation, or after the previous animation has finished
A) animation painter B) timing options C) animation player D) effect options