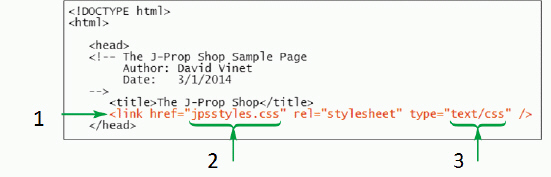
 Item 1 indicated in the figure above is the ____ element.
Item 1 indicated in the figure above is the ____ element.
A. heading
B. body
C. block-level
D. link
Answer: D
You might also like to view...
Firewalls provide ____ services by examining packet headers and allowing traffic that conforms to estalished rules to continue.
A. packet filtering B. NAT C. application proxy D. TCP/IP
The _______ process sets up the file system
Fill in the blank(s) with correct word
A(n) _____ represents the steps in a specific business function or process.
A. relationship diagram B. use case C. data flow unit D. interaction diagram
Critical Thinking Questions Case 2-1 ? Your friend Luis recently was the victim of identity theft and has asked your advice for how to protect himself in the future. Which of the following will you NOT recommend to Luis?
A. Use shopping club and buyer cards. B. Preprint your phone number or Social Security number on personal checks. C. Turn off file and printer sharing on your Internet connection. D. Do not click links in or reply to spam.