Which of the following refers to a successful attempt to compromise a system's security?
A. discovery
B. exploit
C. break-in
D. gateway
Answer: C
Computer Science & Information Technology
You might also like to view...
A(n) __________________ is a graph in which each connection has only one direction.
A. unidirectional graph B. digraph C. TS graph D. TR graph
Computer Science & Information Technology
Table 1 is provided to record the problems discovered in the network configuration. As you find each problem, add the discovered problem to Table 1, along with the actions to be taken to resolve the problem.
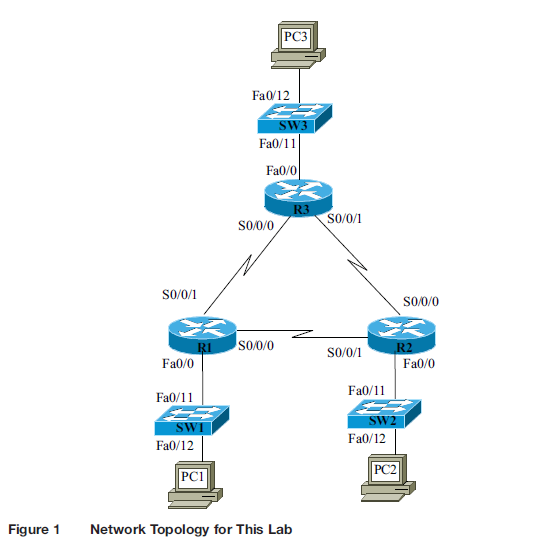
Computer Science & Information Technology
You can undo changes you made to a file by typing u.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
The appropriate software to use for writing and editing research papers is ________ software.
A) spreadsheet B) presentation C) word processing D) database
Computer Science & Information Technology