Match the following terms to their meanings:
I. Protects a computer from hackers and malware A. inbound traffic
II. Tech-savvy person who tries to gain unauthorized access B. exception list
III. Data sent to your computer from other computers on C. outbound traffic
the Internet
IV. Data sent from your computer to another computer on D. firewall
the Internet
V. Used on a computer to ensure that a program will not E. hacker
be blocked
D, E, A, C, B
You might also like to view...
Stream mutable reduction operation ________ creates a new collection of elements containing the results of the stream’s prior operations.
a. combine b. accumulate c. gather d. collect
WEP also does not use a key management, and its what type of key never changes.
What will be an ideal response?
What is the role of a systems analyst in the development of open source software?
What will be an ideal response?
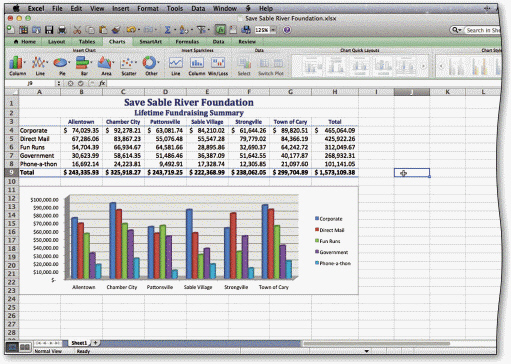 In the accompanying figure, the ____ identifies the colors assigned to each bar in the chart on a worksheet.
In the accompanying figure, the ____ identifies the colors assigned to each bar in the chart on a worksheet.
A. color code B. identifier C. explanation D. legend