Similar to spam, ____ can be annoying, waste people's time, bog down e-mail systems, and clog users' inboxes.
A. computer worms
B. Trojan horses
C. e-mail hoaxes
D. digital manipulation
Answer: C
Computer Science & Information Technology
You might also like to view...
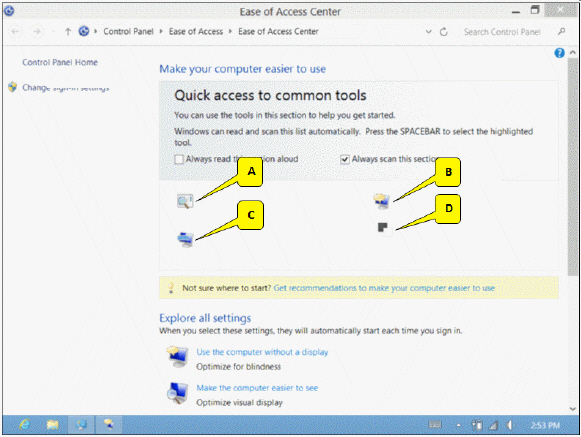 The Ease of Access Center window is shown in the accompanying figure. Some of the accessibility titles are removed and replaced by callouts. Which callout points to the Start On-Screen Keyboard tool?
The Ease of Access Center window is shown in the accompanying figure. Some of the accessibility titles are removed and replaced by callouts. Which callout points to the Start On-Screen Keyboard tool?
A. A B. B C. C D. D
Computer Science & Information Technology
If a machine is infected by a virus, you should disconnect it from the network to stop the virus from spreading
Indicate whether the statement is true or false.
Computer Science & Information Technology
Python programs require two or more modules.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
ISO 27014:2013 is the ISO 27000 series standard for ____________.
A. governance of information security B. information security management C. risk management D. policy management
Computer Science & Information Technology