The ____ are an explicit statement of the expected outcome of each information security activity.
A. controls
B. control objectives
C. control structures
D. control blocks
Answer: B
Computer Science & Information Technology
You might also like to view...
Alice does not provide predefined array operations.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
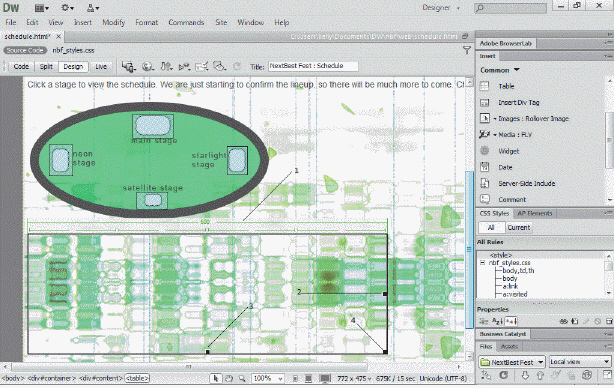 The item marked ____ in the accompanying figure is dragged to change table width.
The item marked ____ in the accompanying figure is dragged to change table width.
A. 1 B. 2 C. 3 D. 4
Computer Science & Information Technology
COGNITIVE ASSESSMENT Your organization has a large number of servers. Which of the following are you most likely to choose as a result?
A. tower server B. blade server C. rack server D. bay server
Computer Science & Information Technology
Which is not one of the four key pieces of personal information you should protect from identity thieves?
A. Social Security number B. Anniversary C. Date of birth D. Street address
Computer Science & Information Technology