A PIN uses
A) At least eight numbers for security
B) Letters and numbers for security
C) A combination of seven letters for security
D) An answer to a security question
B
Computer Science & Information Technology
You might also like to view...
Where should the loop control variable be initialized?
a) before the loop starts b) in the first statement of the loop body c) in the last statement of the loop body d) anywhere in the loop body
Computer Science & Information Technology
The binary representation of the first octet of the IPv4 loopback address is 11111111
Indicate whether the statement is true or false
Computer Science & Information Technology
A pattern like the one in the accompanying figure is an image that is _________________________ to fill a selection or a layer.
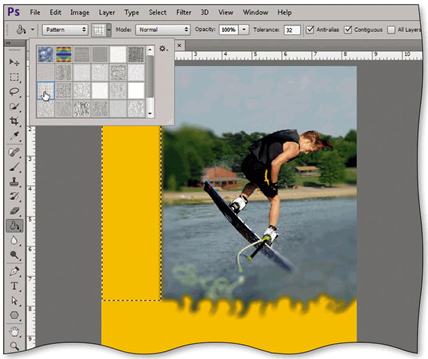
Computer Science & Information Technology
What are snapshot printers?
What will be an ideal response?
Computer Science & Information Technology