The weakest aspect of password-based security is
a. the encryption technique used
b. the type of key chosen
c. the user’s management of their password information
d. the algorithm used
c. the user’s management of their password information
You might also like to view...
The following syntax selects all of the records in the dataset: Dim records = From employee In EmployeesDataSet.tblEmploySelect employee
Answer the following statement true (T) or false (F)
Which of the following statements describes a solution that solves this problem for Cloud Service Consumer A by improving both Cloud A and Cloud B environments?
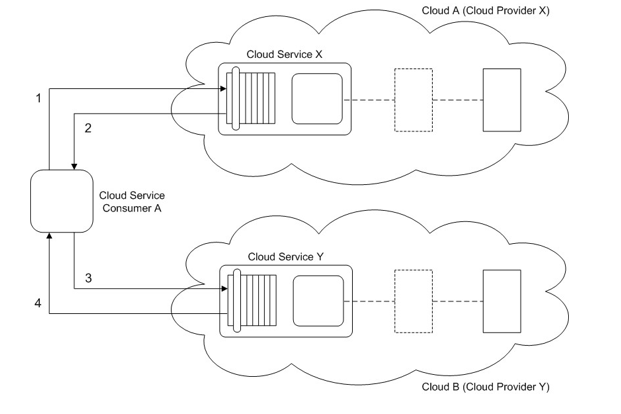
Cloud Service Consumer A accesses Cloud Service X (1) that resides in Cloud A. Cloud Service X processes the request from Cloud Service Consumer A and then sends back a response with the requested data (2). Cloud Service Consumer A then sends a message to Cloud Service Y (3) that resides in Cloud B. The message contains some of the data received from Cloud Service X. After processing the request, Cloud Service Y sends back a response with a success or failure code (4).
Cloud A is a private cloud owned by the same organization that owns Cloud Service Consumer A. Cloud B is a community cloud owned by a group of organizations. The availability rating of Cloud Service X, as indicated in its SLA, is 99.98%. When Cloud Service Consumer A issues a request message to Cloud Service X, it can result in prolonged processes as Cloud Service X attempts to gather the requested data from various data sources. Because Cloud Service X is shared by other cloud service consumers and because the data sources are also shared by other parts of the o
The transition from ____ is initiated by the Job Scheduler according to some predefined policy. At this point, the availability of enough main memory and any requested devices is checked.
A. READY to RUNNING B. RUNNING to WAITING C. RUNNING back to READY D. HOLD to READY
Describe the Fibre Channel (FC) infrastructure used to support a storage area network (SAN).
What will be an ideal response?