The Telnet protocol encrypts transmitted data, which therefore cannot be read by others on the network.
Answer the following statement true (T) or false (F)
False
Computer Science & Information Technology
You might also like to view...
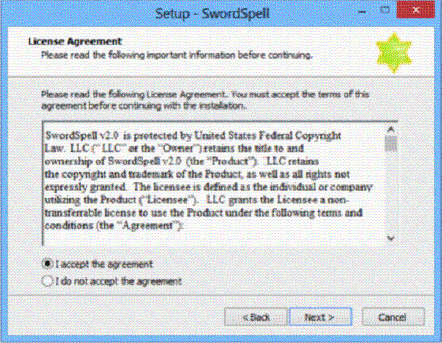 The accompanying figure shows a(n) _____ agreement.
The accompanying figure shows a(n) _____ agreement.
A. EULA B. network license agreement C. single-user agreement D. none of the above
Computer Science & Information Technology
Which of the following selection tools works by automatically detecting the edge of the object you want to select?
a. lasso b. magic wand c. magnetic lasso d. marquee e. polygonal lasso f. quick mask
Computer Science & Information Technology
Describe the structure of a configuration file for OpenSSL.
What will be an ideal response?
Computer Science & Information Technology
Depending on user requirements, a switch can interconnect two different types of CSMA/CD network segments: ____ segments and dedicated segments.?
A. ?shared B. ?remote C. ?local D. ?distributed
Computer Science & Information Technology