The Table Analyzer Wizard can make all the database changes by itself if that is what you desire.
Answer the following statement true (T) or false (F)
True
You might also like to view...
Which of the following is an example of a Severity Level 2 incident?
A) Malware detected on multiple systems B) User’s excessive use of bandwidth or resources C) Compromise or suspected compromise of any company website or web presence D) Compromise or suspected compromise of protected customer information
You can view all of the objects and the order that they are stacked on a layer by expanding the layer.
Answer the following statement true (T) or false (F)
________ is a specification for cryptographically signing e-mail messages, permitting a signing domain to claim responsibility for a message in the mail stream.
Fill in the blank(s) with the appropriate word(s).
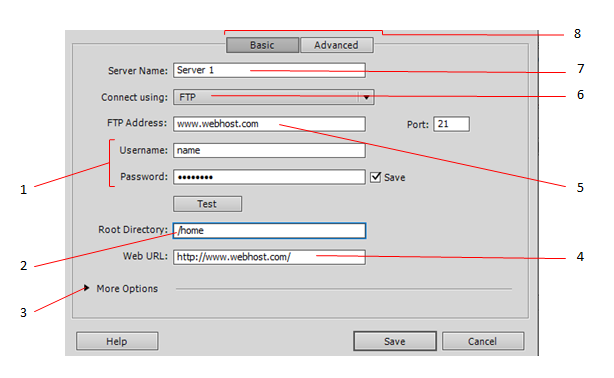
A. 2 B. 3 C. 4 D. 5