Your mobile device is displaying messages informing you that your device is infected with malware. The instructions tell you to install another app to properly remove the malware.
What should you do?
A. Back up all user data and perform a factory reset.
B. Go ahead and install the app to clean the device.
C. Follow the instructions in the message and verify the app site is legitimate.
D. Disregard the message and check for a compromised app.
Answer: D
You might also like to view...
Using the protected keyword also gives a member:
a. public access. b. package access. c. private access. d. block scope.
Which is not a way to proceed when creating a catalog of forms to help you understand the information flow currently in use in business?
A) Collect examples of all the forms in use. B) Note the type of form. C) Document the intended distribution pattern. D) Compare the intended distribution pattern with who actually analyzes the form.
Discuss a situation in which it would be more appropriate to use a do…while statement than a while statement. Explain why.
What will be an ideal response?
Answer the following statement(s) true (T) or false (F)
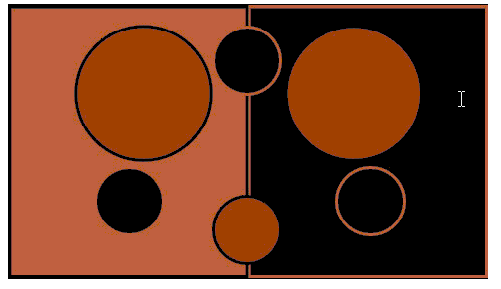
1. In the informal balance shown in the accompanying figure, objects are distributed around the imaginary center point of the composition.
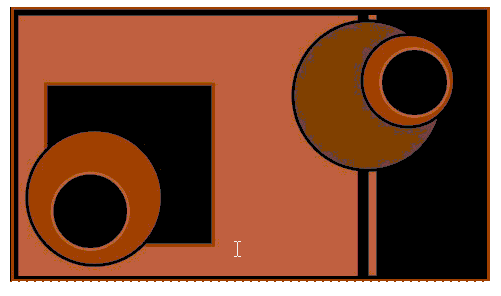
2. The Rule of Thirds, shown in the accompanying figure, states that the most interesting compositions are those in which the strongest element is off center.
3. As demonstrated in the accompanying figure, when you use the Rule of Thirds to design a composition, you divide the page into thirds both horizontally and vertically.
4. As shown in the accompanying figure, when you use the Rule of Thirds to design a composition, no object should take up more than two-thirds of the canvas.