In SSL/TLS, a ________ is a specific set of security methods and options.
cryptographic system standard
cipher suite
chosen set
tuple
cryptographic system standard
cipher suite
You might also like to view...
Answer the following statements true (T) or false (F)
1. Most of the products and standards that use public-key cryptography for encryption and digital signatures use RSA. 2. ECC is fundamentally easier to explain than either RSA or Diffie-Hellman. 3. A number of public-key ciphers are based on the use of an abelian group. 4. Elliptic curves are ellipses. 5. For determining the security of various elliptic curve ciphers it is of some interest to know the number of points in a finite abelian group defined over an elliptic curve.
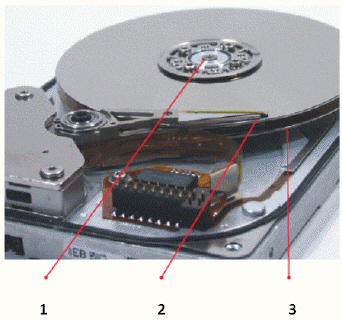 In the accompanying figure of a hard drive, the item labeled 1 is the ____.
In the accompanying figure of a hard drive, the item labeled 1 is the ____.
A. spindle B. read-write head C. platter D. drive bay
____ applications are designed to monitor external requests that are sent to obtain access to the database, and the database environment's responses to these requests.
A. Mixed mode B. Middleware C. Communicator D. Logical
The programs that manipulate the properties of an object are called the object's ____.
A. data B. methods C. algorithms D. parameters