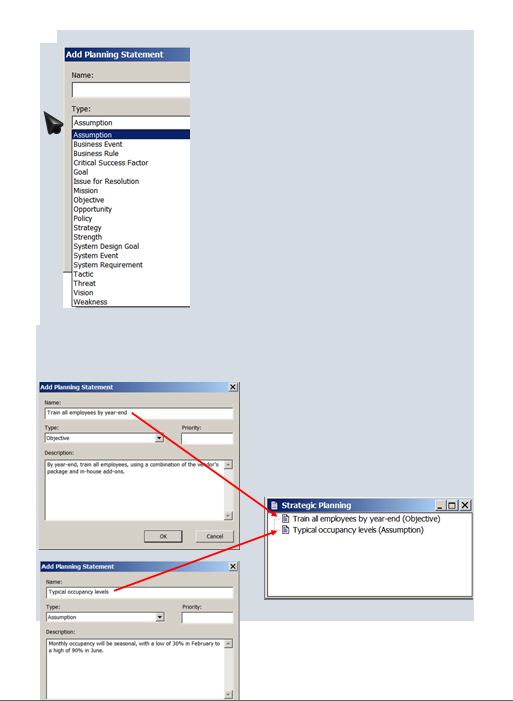
Review the planning example and examine Figure 2-3 on page 44. In that scenario, a systems analyst for a large hotel chain wanted to determine whether the Visible Analyst CASE tool would be helpful in planning a new marketing system. Now, using the same example, create a sample project named HOTEL. Add at least seven sample planning statements, including an assumption, an objective, a critical success factor, strength, a weakness, an opportunity, and a threat. You should try to suggest realistic examples, and you can use your imagination freely.
What will be an ideal response?
We suggest that you share these examples with students, either live in a seated class, or with a series of slides or other Web-based techniques if you are teaching an online class.
The first screen shows the types of planning statements that can be added.
The next screens show examples of two statements: an assumption and an objective. Using Visible Analyst, students should be able to build on these examples and create an appropriate, real-world set of planning statements applicable to the hotel scenario.
You might also like to view...
Match each term with the correct statement below.
A. A perimeter that incorporates all items that will be secured B. Explicit behaviors implemented to achieve a desired outcome C. The generic organizing and control principles that an organization uses to underwrite the management of its information function D. Assurance that the security actions of the organization directly support its goals E. The tendency for organizational activities to become disorganized over time due to competitive pressure and technological change F. The level of assessed competence of the management process G. Decision making that is supported by empirically derived data H. Quantitative measures of security performance I. The prescribed activities to achieve the long-range intentions of the organization
Implicit personalization techniques capture user-provided information, such as information from warranties, surveys, user registrations, and contest-entry forms completed online.
Answer the following statement true (T) or false (F)
Choose the HTML tag below that would configure a scrolling text box with the name "feedback", 3 rows, and 60 characters.
a. ``` ``` b. ``` ``` c. ``` ``` d. none of the above
Describe two of the three methods of analog modulation.
What will be an ideal response?