Evaluate the distance formula 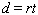 using the given values of the variables. Round your answer to the nearest tenth, if necessary.
using the given values of the variables. Round your answer to the nearest tenth, if necessary.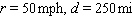
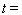 __________
__________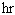
Fill in the blank(s) with the appropriate word(s).
Answer: 5
Computer Science & Information Technology
You might also like to view...
network switches nowadays have a feature to safeguard against non-legitimite DHCP servers. It is called which of the following?
What will be an ideal response?
Computer Science & Information Technology
From a network security perspective, the ____ logs are the most valuable to a systems and network administrator in identifying and resolving issues.
A. admin and operational B. applications and services C. analytic and debug D. admin and analytic
Computer Science & Information Technology
Describe software VPN systems.
What will be an ideal response?
Computer Science & Information Technology
In C++, a variable or symbolic constant must be ____________________ before it has been used.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology