____________________ is the practice of sending an identical e-mail repeatedly to the target user.
Fill in the blank(s) with the appropriate word(s).
E-mail bombing
You might also like to view...
Which of the following is the correct way to declare a variable that represents a price?
a. declare double price = 0; b. int price = 0; c. Integer price = 0.0; d. double PRICE = 0.0; e. double price;
Which statement about USB ports is TRUE?
A) They are being replaced by parallel ports. B) They are used to connect computers to a local network. C) They transfer information wirelessly. D) USB ports are used with different types of devices.
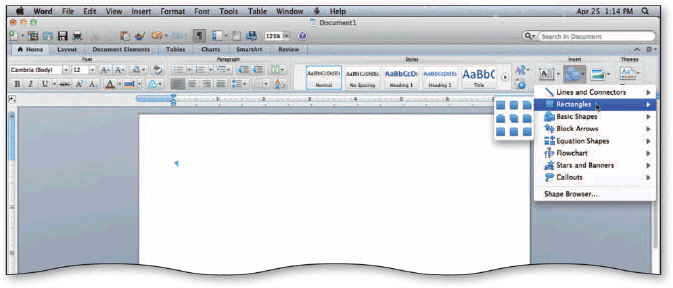 As shown in the accompanying figure, Word has a variety of predefined shapes, which are a type of drawing object, that you can insert in documents.
As shown in the accompanying figure, Word has a variety of predefined shapes, which are a type of drawing object, that you can insert in documents.
Answer the following statement true (T) or false (F)
Proxy servers, like packet filters, can filter out content based on rules that contain a variety of ____________________.
Fill in the blank(s) with the appropriate word(s).