Which of the following is used with Windows to secure data from unauthorized users?
A) REGEDIT
B) Compression
C) EFS
D) Network Neighborhood
C
You might also like to view...
MC The last line number in a traceback indicates the__________ .
a) throw point. b) catch point. c) handle point. d) None of the above.
The _________________________ is a program on a read-only or flash memory chip that establishes basic communication with components such as the monitor and disk drives.
Fill in the blank(s) with the appropriate word(s).
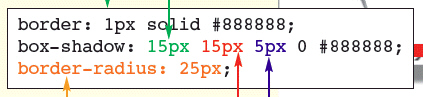 As shown in the accompanying figure, a positive h-shadow value pushes the shadow ____.
As shown in the accompanying figure, a positive h-shadow value pushes the shadow ____.
A. to the left B. up C. down D. to the right
Which of the following statements about full interruption tests is true?
A. It is considered a true/false test. B. It is a passive type of test. C. During the test key personnel performs a dry run of the emergency. D. Backup processing occurs in parallel with production services that never stop.