802.1X combines RADIUS-style AAA with which of the following to make a complete authentication solution?
A. PPP
B. MS-CHAP
C. EAP
D. TLS
Answer: C
You might also like to view...
Any intangible asset that consists of human knowledge and ideas is _______.
A. cyber property B. personal property C. intellectual property D. real property
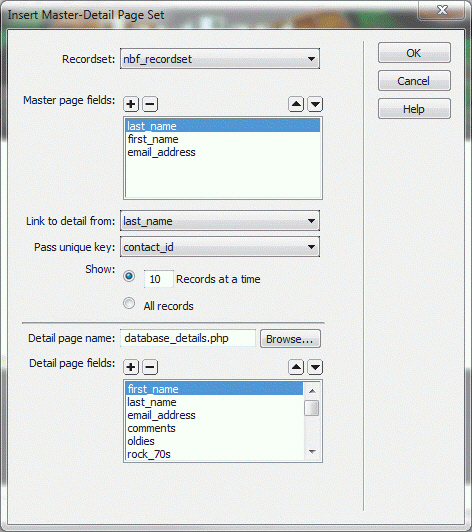 To display the dialog box shown in the accompanying figure, in the ____________________ category of the Insert panel, click the Master Detail Page Set button.
To display the dialog box shown in the accompanying figure, in the ____________________ category of the Insert panel, click the Master Detail Page Set button.
Fill in the blank(s) with the appropriate word(s).
An OpenOffice Calc spreadsheet consists of one or more individual ________
Fill in the blank(s) with correct word
In an Append query, what happens to any records that violate the Primary key (or any other) rule?
A) The records are rejected. B) A message box appears telling you that you must fix the problematic records before the query can be run. C) New Primary key values are added to the records D) The query pauses at each violating record and allows you to fix the error(s).