How are power-on passwords normally removed?
A) Through software
B) By using a special disk
C) By booting from a different device
D) By jumpering two pins together on the motherboard
D
You might also like to view...
This can result in network issues or loss of network connectivity of the computer. It is always a good idea to create a firewall rule and try it out, one at a time.
What will be an ideal response?
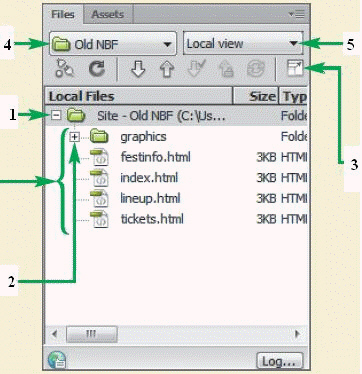 In the accompanying figure, click the item marked ____ to switch to the remote site files.
In the accompanying figure, click the item marked ____ to switch to the remote site files.
A. 2 B. 3 C. 4 D. 5
The first line of a method (including the return type, the method name and the parame- ter list) is known as the method
a) body b) title c) caller d) header
The ___, which makes technical recommendations about data communication interfaces, took on the task of creating a universal network architecture, resulting in the OSI Reference Model.
A. IEEE 802 Committee B. High-Level Data Link Organization C. International Organization for Standardization D. Transmission Control and Internet Committee